Information security
As one of the Yaskawa Group Code of Conduct, Yaskawa is committed to ensuring thorough information security. Based on this code, we will ensure the protection of not only our own information but also other companies’ important and personal information, as well as prevent the disclosure of confidential information and insider trading.
In order to implement this code, Yaskawa has set forth the following items in “Our Commitments” in the Yaskawa Group Code of Conduct Guidance.
Relevant items in the Yaskawa Group Code of Conduct
4. Yaskawa Group respects intellectual property rights such as patent rights, copyrights and trademark rights by protecting its own rights and not infringing the rights of others.
5. Yaskawa Group’s policies and procedures protect not only its own information but also important information of other companies and personal information. Yaskawa Group also discourages and tolerate no insider trading.
6. Yaskawa Group complies with company information disclosure rules and strive to disclose correct information in a timely manner.
7. Yaskawa Group creates and stores information properly and records the grounds for making key business judgments and decision-making in the course of operations appropriately.
Yaskawa Group Information Security [Basic Policy]
Protection and Maintenance of Management and Customer Information Assets by Zero Trust Security
Basic Idea
With “zero trust security” in mind, we will carry out robust information security management activities that are not affected by the external environment of the entire global Yaskawa Group. Specifically, in our YASKAWA Digital Transformation (YDX) promotion activities centered on i3-Mechatronics, we will appropriately implement security measures and emergency responses for the YASKAWA Data Lake, the storage location of our management and customer information assets, and our internal systems, while strengthening threat intelligence monitoring and response globally. Taking information as management resources, we will work to protect and continuously maintain our management and customer information assets from threats such as accidents, disasters, and crimes based on the following policies.
Management Responsibility
Yaskawa strives to systematically and continuously improve information security under the leadership of management.
Development of Internal Systems
Yaskawa establishes roles and responsibilities related to information security, establishes an organization for maintenance and improvement, and establishes a system to manage and operate it systematically.
Response to Risk Assessment
In order to define the risk level and take appropriate information security measures according to the level, Yaskawa conducts multi-purpose risk analysis and risk assessment of threats and vulnerabilities. We will also continuously improve our information security measures based on the results of the risk assessment.
Employee Initiatives
Yaskawa ensures that all employees fully understand that protecting management and customer information assets is fundamental to Yaskawa’s business continuity activities and an important corporate social responsibility, and provides appropriate education and training to all employees.
Compliance with Legal Requirements
Yaskawa complies with and respects the obligations of laws, regulations and guidelines related to information security.
Response to Information Security Incidents and Accidents
When an incident involving information security occurs, Yaskawa promptly investigates the cause and implements countermeasures to minimize the impact. We also take appropriate measures, including preventive measures and recurrence prevention of information security incidents.
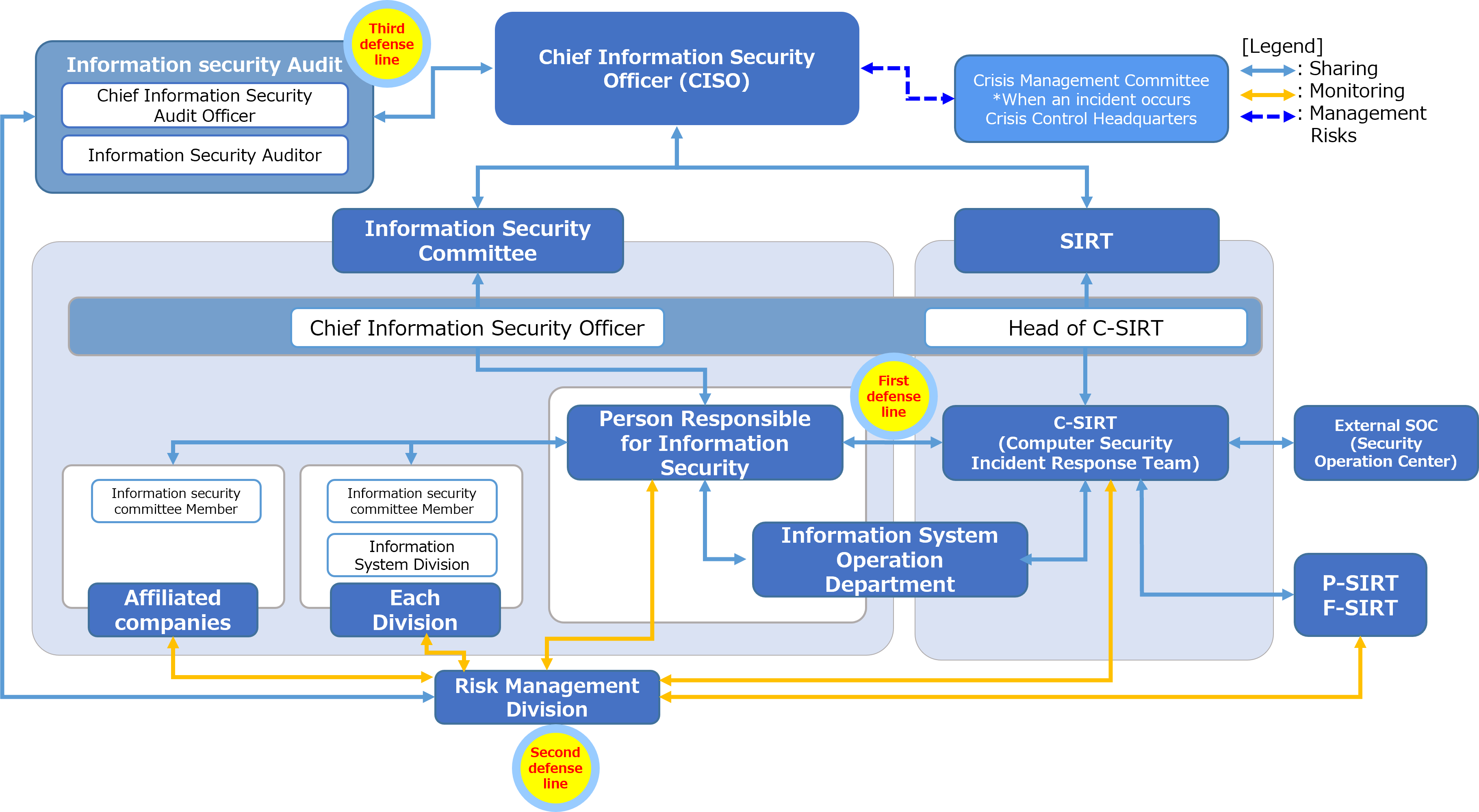
Information Security System
The information security system is managed by the Information Security Committee under the Chief Information Security Officer (CISO), and promotion officers are assigned to each global location, business division and subsidiary to enhance information security system.
We are also strengthening our three-line defense system by incorporating an external Security Operation Center (SOC).
Status of Response to Data Breaches and Incidents
With the ongoing activities of the internal CSIRT organization, there have not been any serious data breaches or incidents that could affect company management. (As of February 2025) In addition, daily security measures are in place against ransomware and targeted attack e-mails preventing infection or business impact.
Training Employees on Risks and Responses Related to Data Security and Privacy
We have established the Company Information Management Rules to eliminate risks and conduct business activities safely when handling information assets, including personal information. These Regulations set forth a code of conduct for officers and employees (including subcontractors) concerning information security. Based on this, the Company has prepared a Company Information Management Manual, which defines the level of confidential information of data received from customers and internally processed data, and operates it according to business processes from creation, acquisition, and the definition of scope of disclosure to disposal.
We have also established the Information Systems Management Division and the SIRT Division under the CISO to strengthen security. The main measures taken against unauthorized access and cyber attacks include strengthening the security of file transactions with external parties (manager approval and automatic data encryption), internet isolation, internal system defense using security appliances, 24 hour monitoring using the Security Operations Center (SOC), and training for responding to targeted e-mail.
We have also established the Information Systems Management Division and the SIRT Division under the CISO to strengthen security. The main measures taken against unauthorized access and cyber attacks include strengthening the security of file transactions with external parties (manager approval and automatic data encryption), internet isolation, internal system defense using security appliances, 24 hour monitoring using the Security Operations Center (SOC), and training for responding to targeted e-mail.
We also conduct an information security e-learning program for the group employees in Japan once a year to raise awareness of information security among employees.
In addition, once a month, with the aim of improving information security awareness, internal reporting is made on the status of implementation of preventive measures against risks, occurrence of incidents, and response status.
 Region
Region



 Principles & vision
Principles & vision
 Procurement
Procurement
 Sustainability for the Yaskawa Group
Sustainability for the Yaskawa Group
 Customer satisfaction
Customer satisfaction
 Supply chain
Supply chain
 Social contribution
Social contribution
 Compliance & risk management
Compliance & risk management